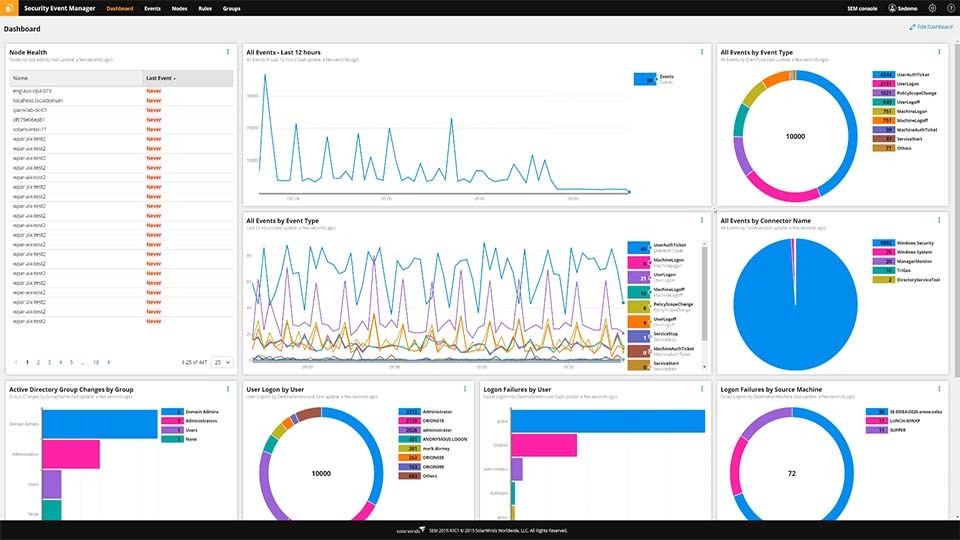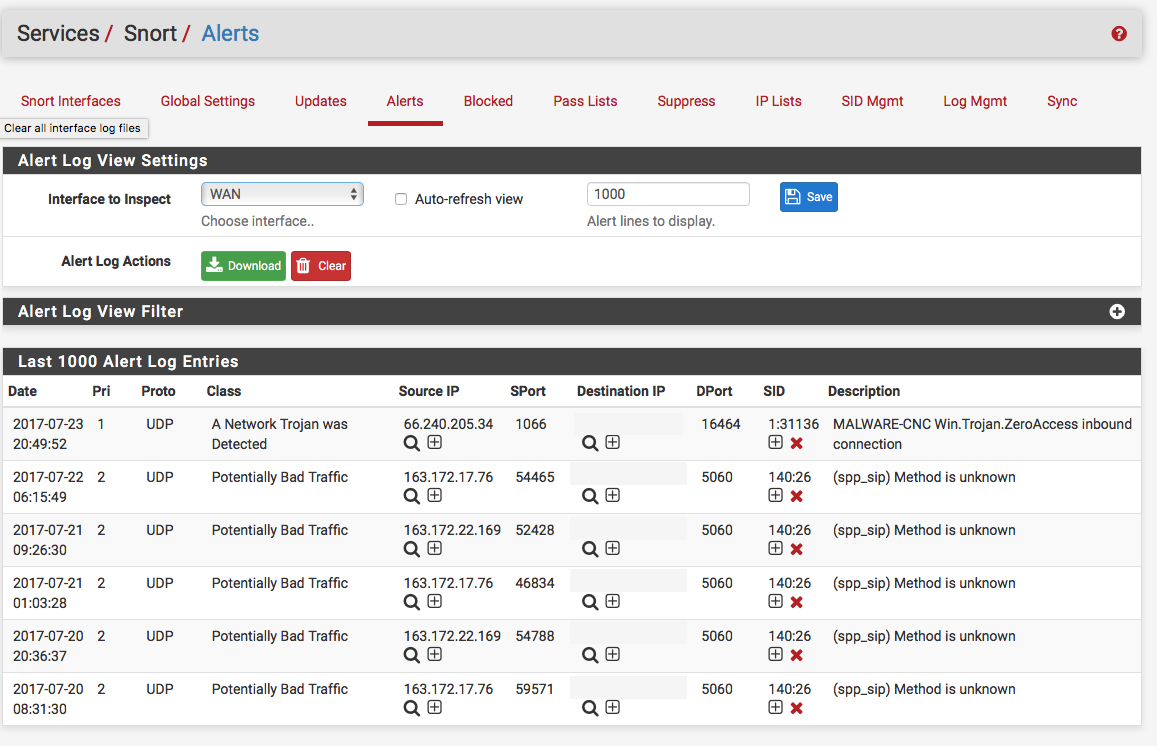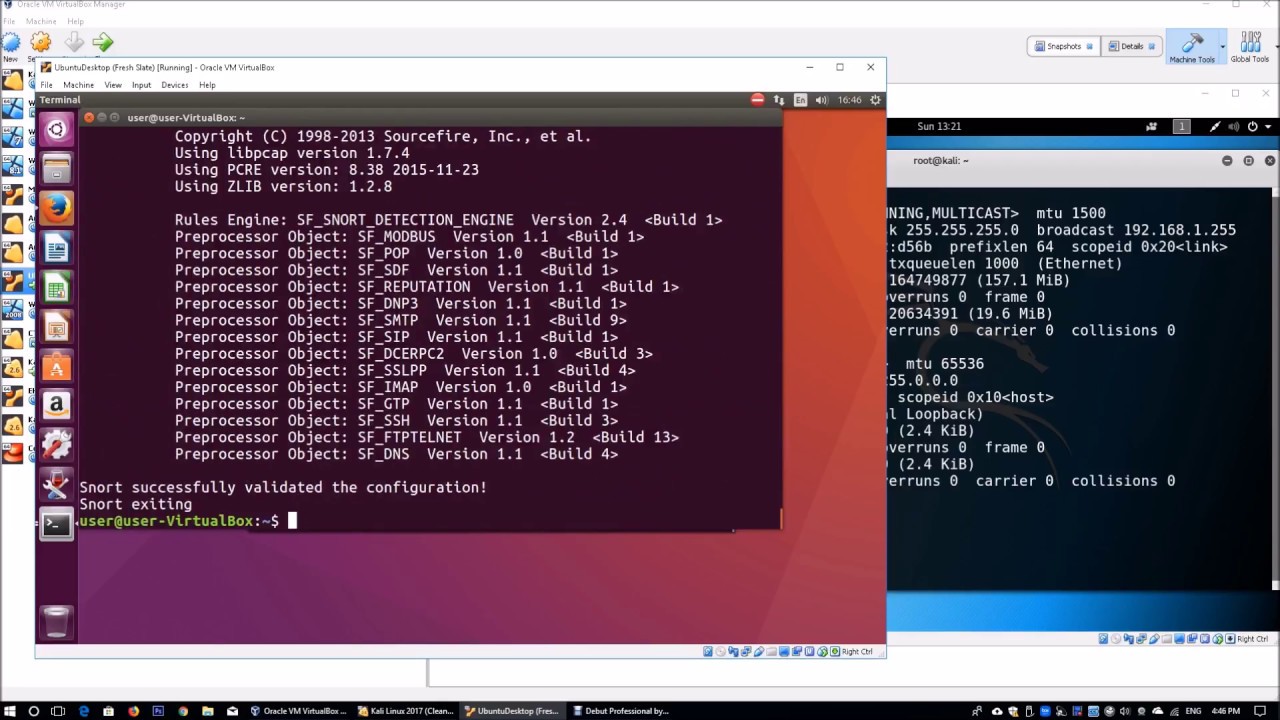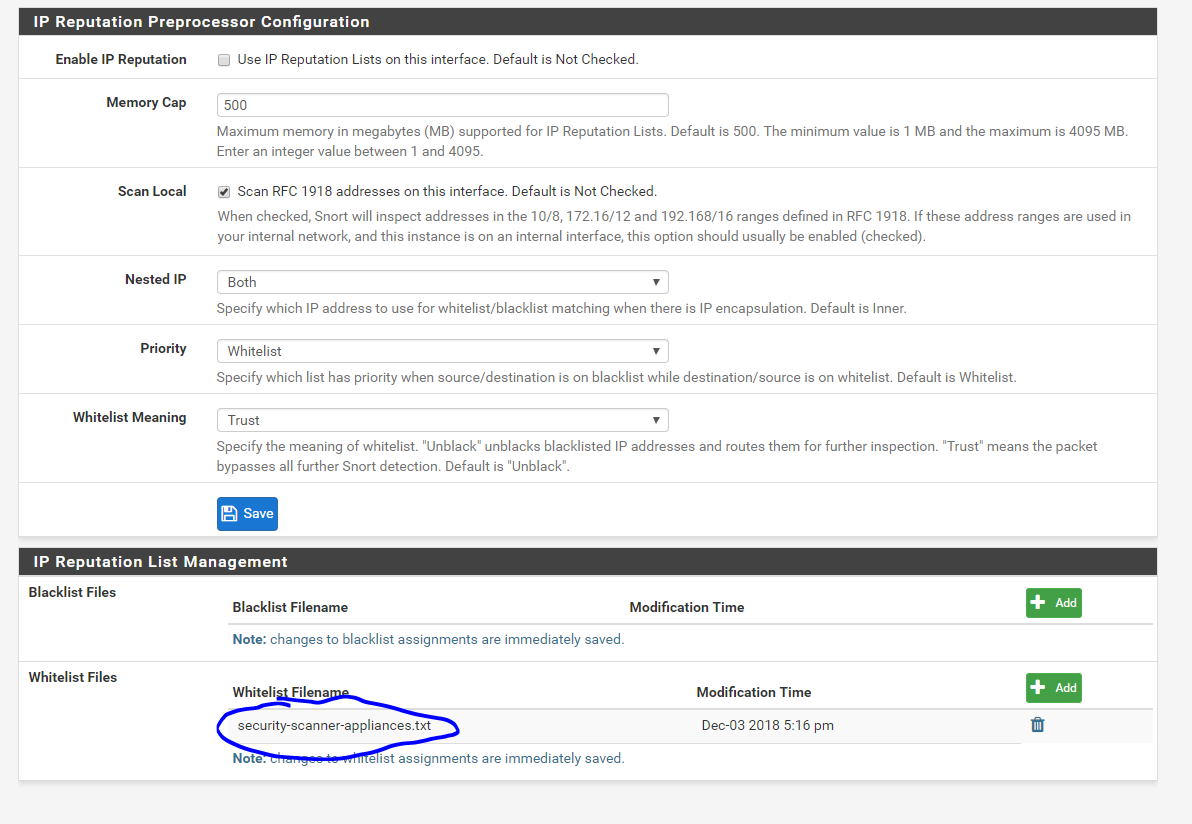
Snort: Whitelist a vulnerability scanner that scans internal addresses on other interfaces (SOLVED) | Netgate Forum
![PDF] Rule-Based Network Intrusion Detection System for Port Scanning with Efficient Port Scan Detection Rules Using Snort | Semantic Scholar PDF] Rule-Based Network Intrusion Detection System for Port Scanning with Efficient Port Scan Detection Rules Using Snort | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ce0229f8e85305f52e759d172b00adecc626dbbc/5-Figure4-1.png)
PDF] Rule-Based Network Intrusion Detection System for Port Scanning with Efficient Port Scan Detection Rules Using Snort | Semantic Scholar
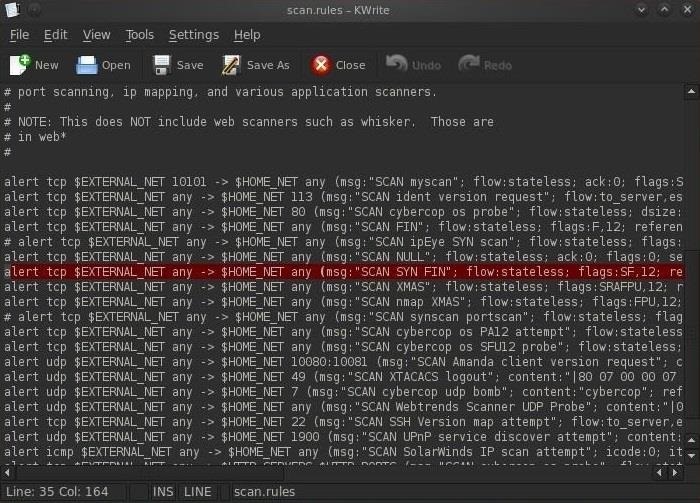
![Topera] The IPv6 port scanner invisible to Snort (IDS) Topera] The IPv6 port scanner invisible to Snort (IDS)](https://1.bp.blogspot.com/-hzTPQFQ7r4M/UWxq3H3QJNI/AAAAAAAAAdo/AAafBA7T8IQ/s1600/topera_execution.jpg)
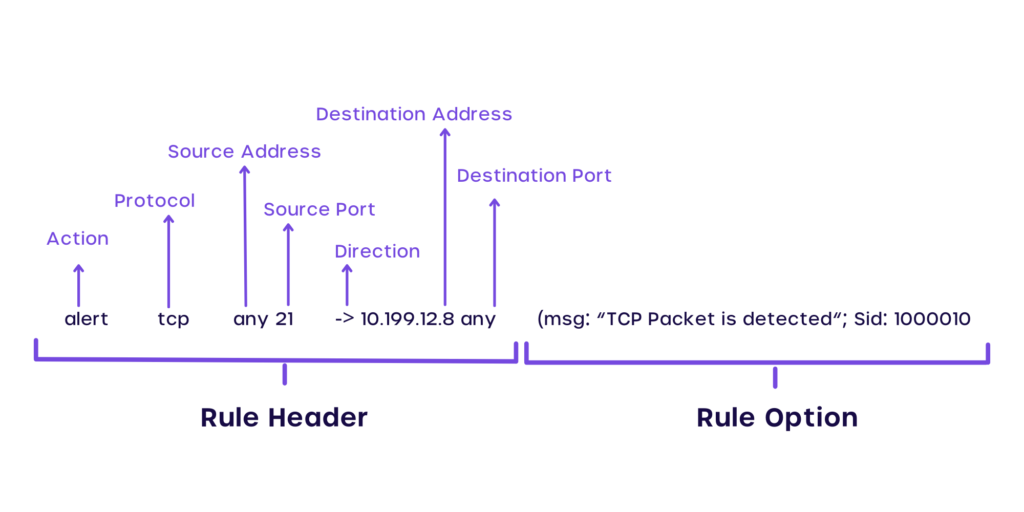
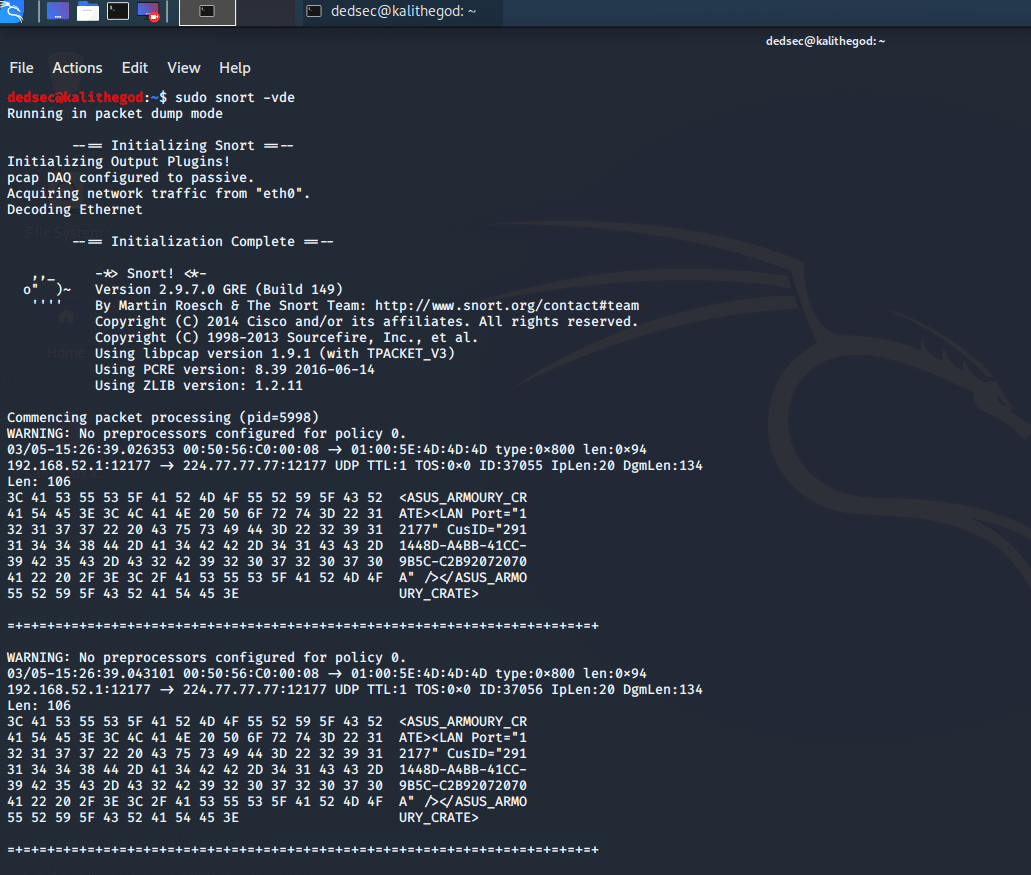


![Basic snort rules syntax and usage [updated 2021] | Infosec Resources Basic snort rules syntax and usage [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/032516_1127_SnortLabMan31.png)